A de-synchronization attack on Gossamer
4.7 (777) · $ 7.00 · In stock

Three time bombs lurking in your network - Connectis

PDF) Gossamer: weaknesses and performance
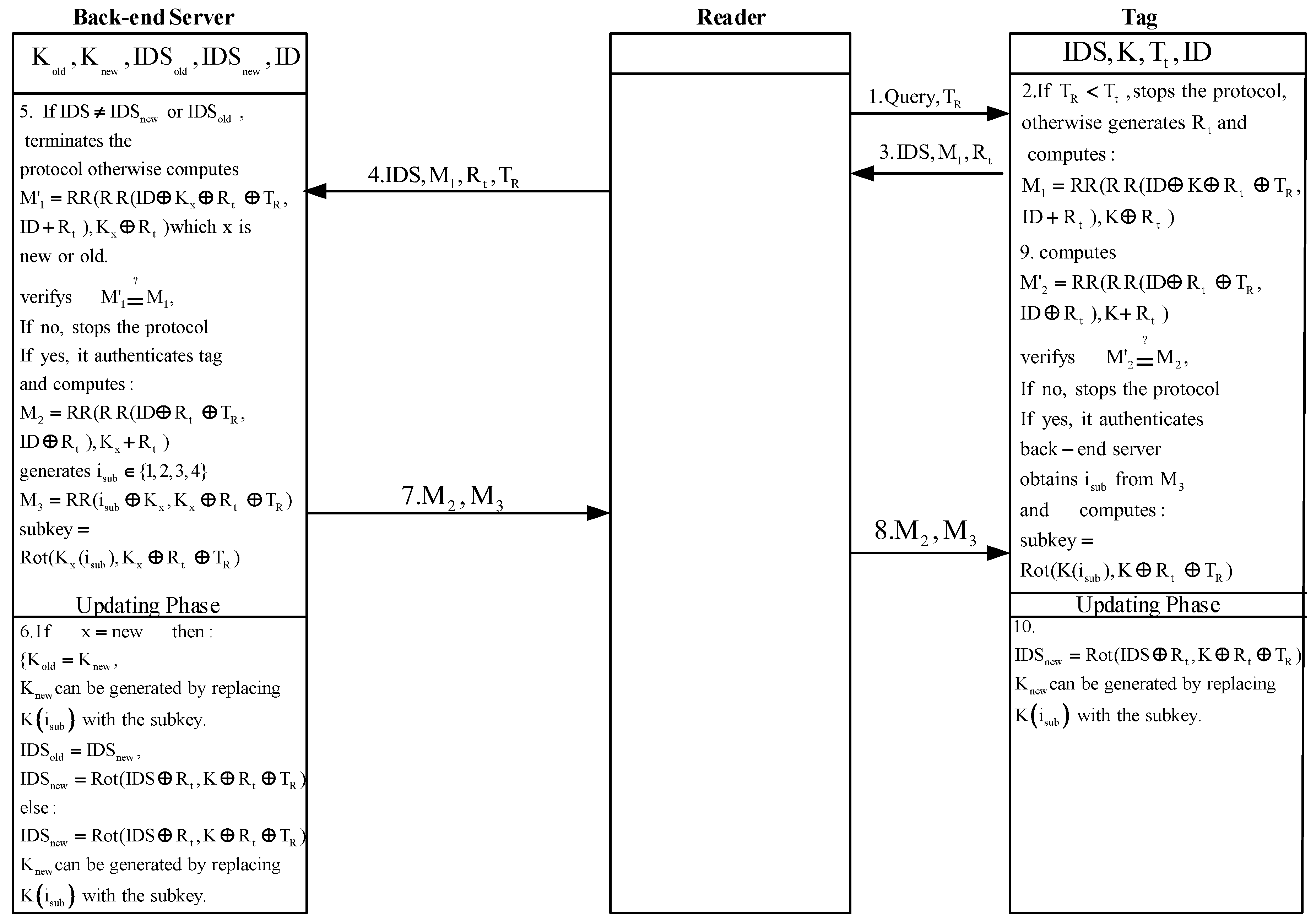
Future Internet, Free Full-Text

014ac81c353cbd3b48eaa54f0a52ff3a0c072cb5.png
Nectar (PolySwarm) (NCT) Overview - Charts, Markets, News

new releases – Page 3 – Reckless Records

Riffs – Biblioklept

Gossamer: weaknesses and performance International Journal of Information Security

Zahra EBADI ANSAROUDI, Doctor of Philosophy, Fondazione Bruno Kessler, Trento, FBK, Applied Cryptography

PDF) Gossamer: weaknesses and performance

Zahra EBADI ANSAROUDI, Doctor of Philosophy, Fondazione Bruno Kessler, Trento, FBK, Applied Cryptography

PDF] Generalized Desynchronization Attack on UMAP: Application to

Sensors, Free Full-Text

Digital Forensics in Small Devices: RFID Tag Investigation
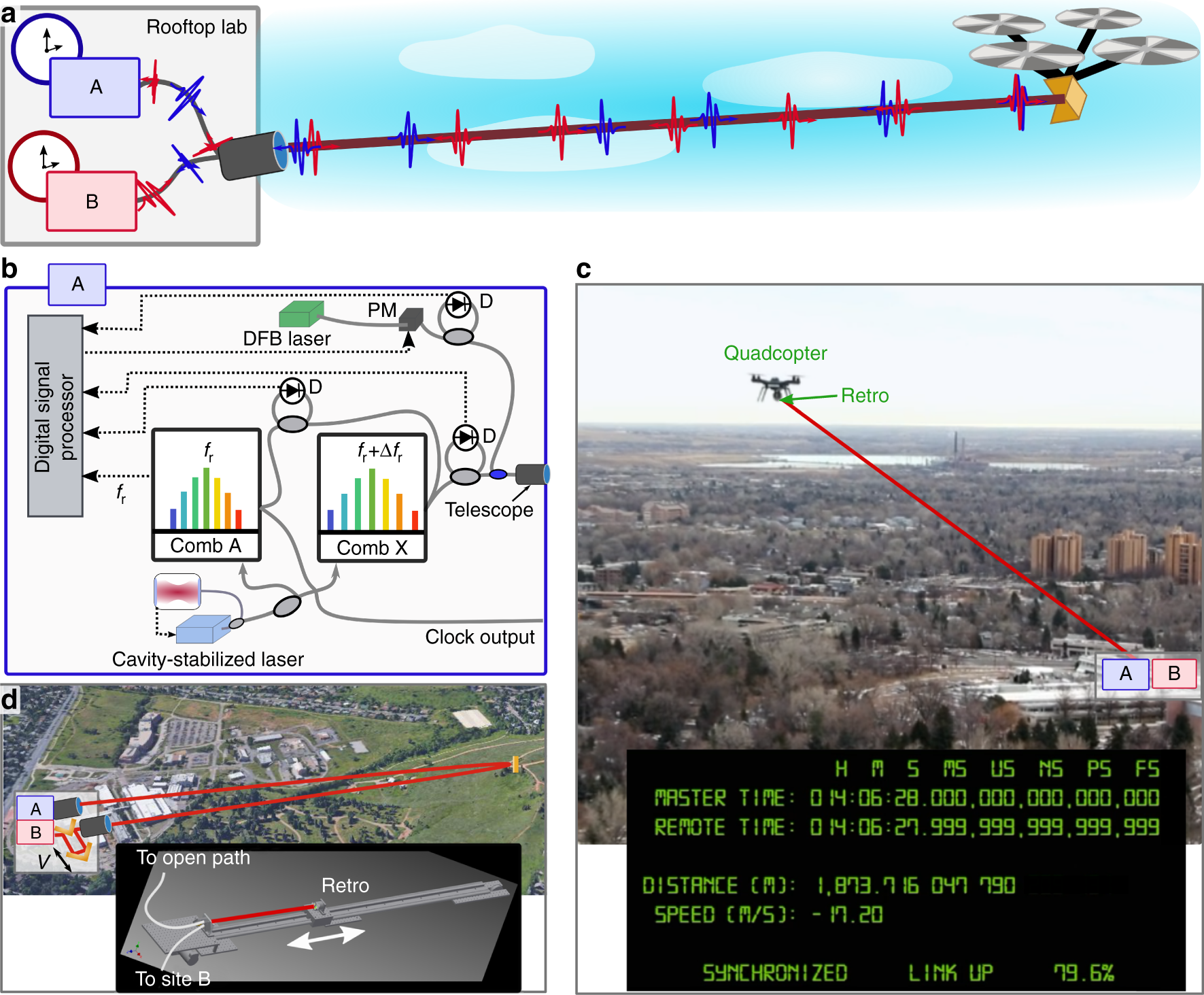
Femtosecond time synchronization of optical clocks off of a flying












